ZFS can be configured to use Oracle Key Vault (OKV) as a KMIPs cluster to store it's encryption keys. In this blog post I will go through how to configure my ZFS replication pair to utilize my OKV cluster and take advantage of the Raw Crypto Replication mode introduced in 8.8.57.
OKV Cluster Environment:
First I am going to describe the environment I am using for my OKV cluster.
I have 2 OKV servers, OKVEAST1 ( IP:10.0.4.230) and OKVEAST2 (IP: 10.0.4.254). These OKV servers are both running 21.6 (the current release as of writing this post).
ZFS replication Pair:
For my ZFS pair, I am using a pair of ZFS hosts that I have been running for awhile. My first ZFS host is "testcost-a" (IP: 10.0.4.45) and my second ZFS host is "zfs_s3"( IP: 10.0.4.206). Both of these servers are running the 8.8.60 release.
For my replication, I already have "testcost-a" configured as my upstream, and "zfs_s3" configured as the downstream.
Steps to configure encryption using OKV
Documentation:
The documentation I am using to configure ZFS can be found in the 8.8.x Storage Administrators guide. I did look through the documentation for OKV, and I didn't find anything specific that needs to be done when using OKV as a KMIP server.
Step #1 - Configure endpoints/wallets in OKV
The first step is to create 2 endpoints in OKV and assign a shared wallet between these 2 endpoints.
I am starting by creating a single wallet that I am going to use share the encryption keys between my 2 ZFS replication pairs. I
The next step after creating the wallet is to create the 2 endpoints. Each ZFS host is an endpoint. Below is the screenshot for adding the first node.
Then I click on each endpoint and ensure that
- The default wallet for each endpoint is the "ZFS_ENCRYPTION_KEYS" wallet
- The endpoint has the ability to manage this wallet.
Server Enrollment Token
ZFS_S3 FdqkaimSpCUBfVqV
TESTCOST-A uy59ercFNjBisU12
I then go to the main screen for OKV and click on the enrollment token download
You see that the token is validated. Then click on Enroll and it will download the token "okvclient.jar" which I am renaming to okvclient_{zfs server}.zip. This will allow me to extract the certificates.
| Image may be NSFW. Clik here to view.  |
Step #2 - Add the Certificates
After uploading it I then add the "cert.pem" certificate in system also.
After uploading, I clicked in the pencil to see the details for the certificate.
NOTE: The IP Address is the primary node in my OKV cluster.
Under Certificates=>Trusted I uploaded the CA.pem certificate.After uploading this certificate, I click on the pencil and select "kmip" identifying this certificate to be used for the KMIP service.
I can now upload the certificates for my other ZFS server (zfs_s3) the same way.
Step #3 - Add the OKV/KMIP service
Step #4 - Add one or more keys.
After adding it, the key appears in this section.
Step #5 - Add the keys to the shared wallet
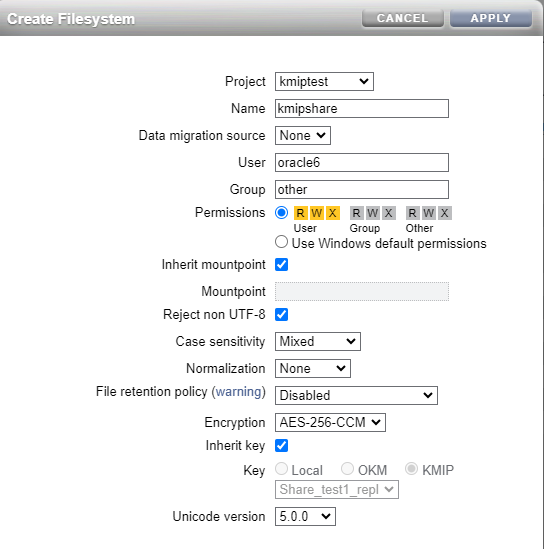
Step #6 - Create a new encrypted project/share
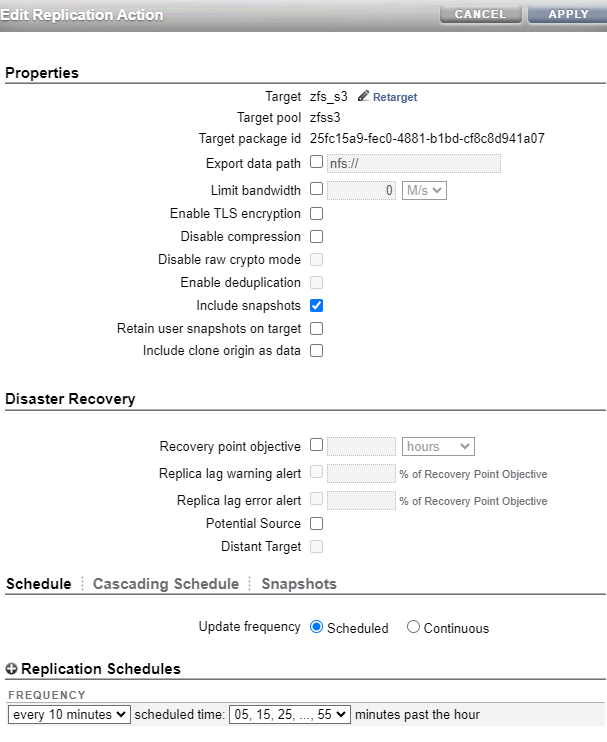
Step #7 - Configure replication
Result:
I now have replication on my encrypted share working between my upstream and downstream. With this new feature, the blocks are sent in their original encrypted format, and are stored on the downstream encrypted. Since both ZFS servers can access the encryption key, both servers are able to decrypt the blocks.